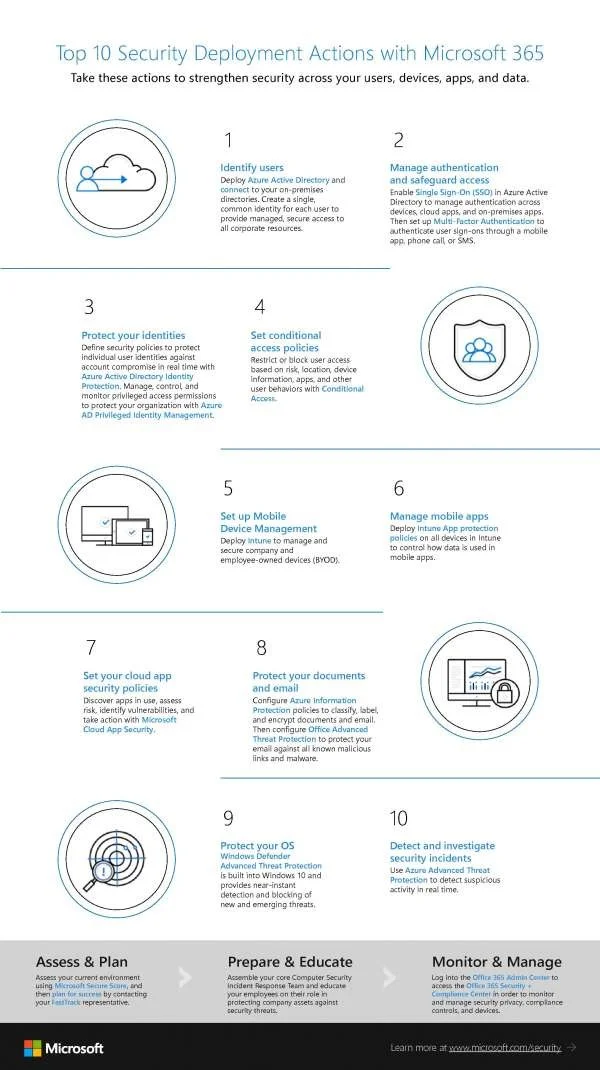
Top 10 Security Deployment Actions with Microsoft 365
Threats come from all areas, from malware attacks to compromised user credentials, and even accidental data leaks caused by human error. Naturally, it follows that an effective security system should have tools to cover all these areas. Using tools like Azure Active Directory and Single Sign On, you can protect your system from common user credential problems while Azure Information Protection can keep your data encrypted and secure even if it's shared outside of your system. We understand the security problems facing your business are far from simple, which is why our multifaceted solution contains tools to address each one.